Dradis Framework is a collaboration and reporting tool for information security teams to manage and deliver the results of security assessments, in less time and with less frustration than manual methods.
Liquid Dynamic Content in Word and HTML reports
We have already supported Liquid content in Dradis Gateway templates for a while – now we are bringing Liquid Dynamic Content to Word and HTML reports as well.
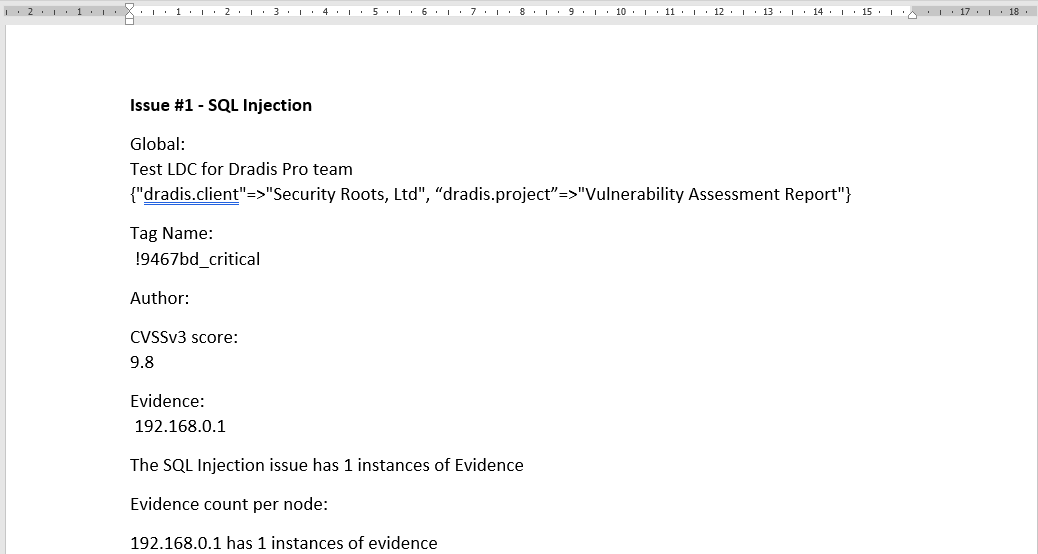
Want to refer to document properties like dradis.client inside a ContentBlock? Want to show the count of evidence inside the text of an Issue? Want to use conditionals like “If this property is in Spanish, export this issue in Spanish instead of English”? Now you can! For example, the following will export into an Issue:
#[Description]#
Global:
{{ project.name }} for {{ team.name }} team
{{document_properties.available_properties}}
Tag Name:
{% for tag in issue.tags %} {{ tag.name}} {%endfor%}
CVSSv3 score:
{{ issue.fields['CVSSv3.BaseScore'] }}
Evidence:
{% for evidence in issue.evidence %} {{ evidence.fields["Label"] }} {%endfor%}
The {{ issue.title }} issue has {{ issue.evidence.size }} instances of Evidence
Evidence count per node:
{% for node in issue.affected %}
{{ node.label}} has {{node.evidence.size}} instances of evidence
{% endfor %}It would give a result like the following:
Better filters in Word templates
We now have two more filtering options available in Word: Filters with spaces, and filters on Nodes.
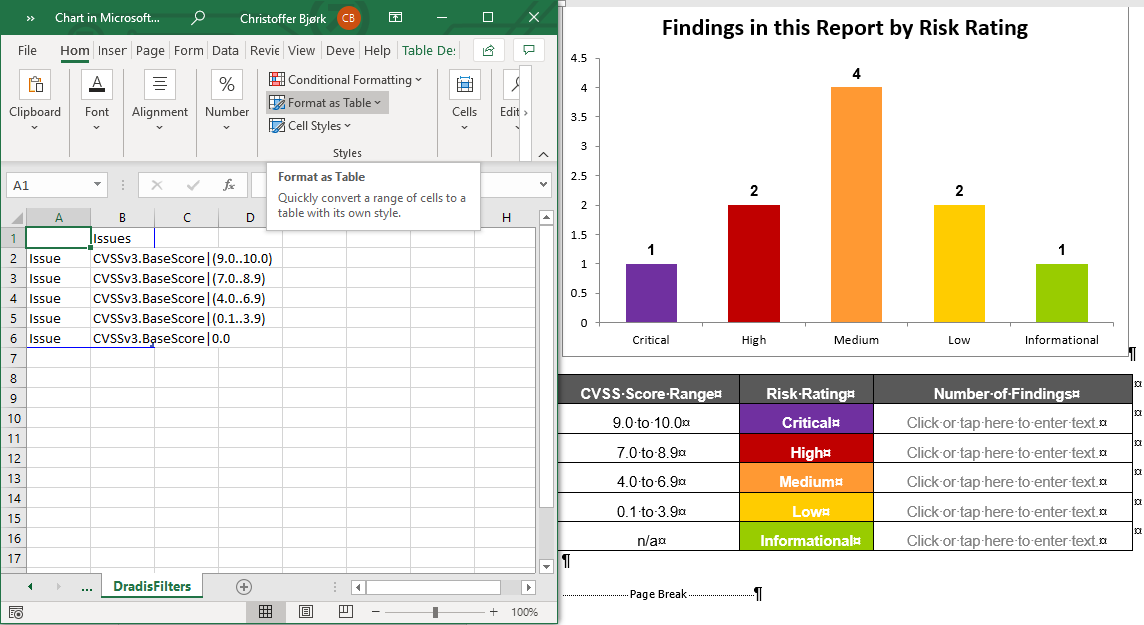
Filtering with spaces means you can use double quotes in both field names and filter values. For example, you can filter by "CVSS Base"|(9.0..10.0) or Category|"A1 Injection".
Nodes can be filtered by Node Properties. For example, if you have a Node property for type with values of internal/external, you can filter a Node by type|internal to only see content for internal-type Nodes.
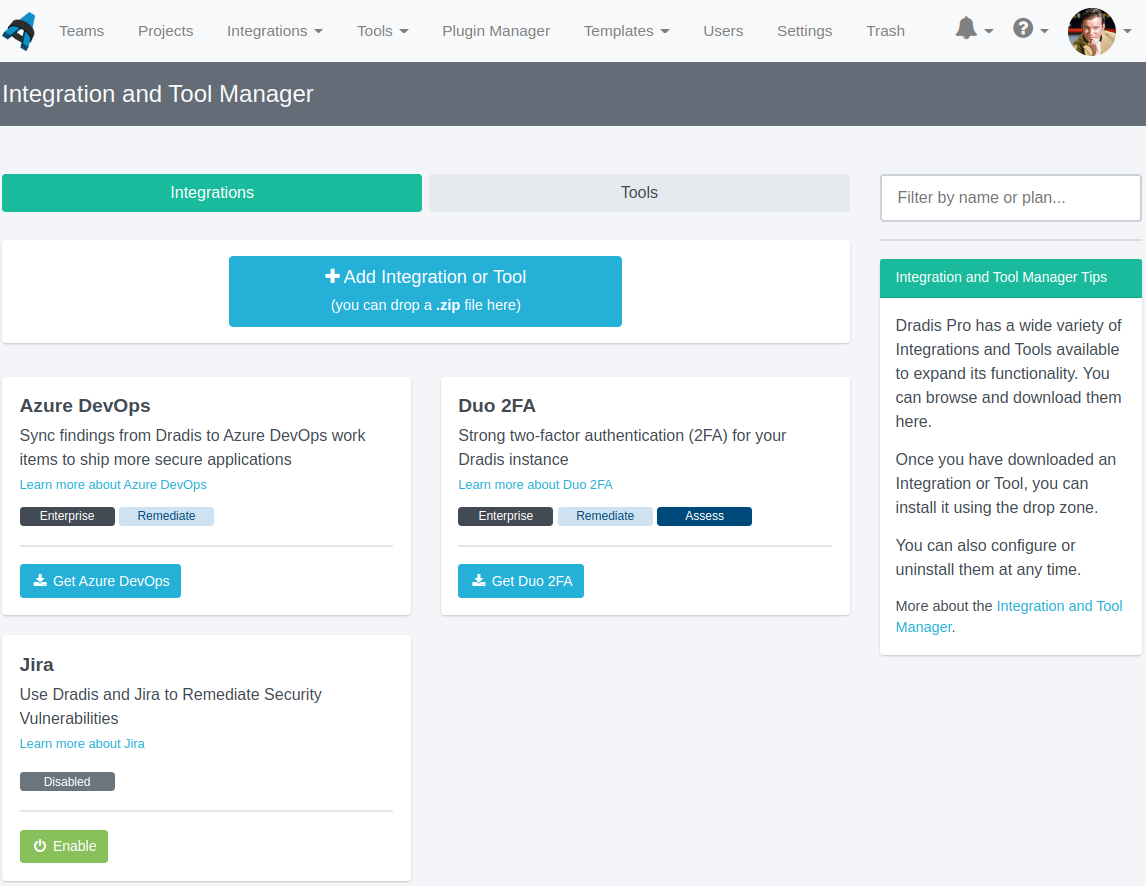
DuoWeb and ServiceNow support in the Integration Manager
We have changed the way our integrations work, so you can now install DuoWeb and ServiceNow right in the Integration Manager. No need to use the command line to install 2FA! You can also configure Duo and ServiceNow, as well as integrations like Azure DevOps, right in the Integration Manager.
Release Notes
- AccessTokens: allow the storage of per-user encrypted tokens
- QA: Show state changes in activity feed
- Sessions: Store :secret_key_base in encrypted configuration file
- Tylium: Extend support for Liquid Dynamic Content
- Upgraded gems:
- bootstrap, popper_js, simple_form
- Bugs fixes:
- Issue Library: Prevent rendering navbar over top of the fullscreen editor
- QA: Redirect to correct view when changing states on QA edit views
- Users: Force logout for users with locked accounts
- Integration enhancements:
- Acunetix: Parse inline code, not just code blocks
- Burp: Adds strong and code tags parsing
- CSV: Fix CSV Upload for files with special characters
- Nessus:
- Parse code tags as inline code
- Add plugin_type as an available Issue field
- Nexpose:
- Parse inline code, not just code blocks
- Wrap ciphers in the
ssl-weak-message-authentication-code-algorithmsfinding
- Qualys: Adds Request/Response Evidence fields for Web Application Scans (WAS)
- Azure DevOps: Switch authentication from PAT to OAuth2
- Duo 2FA:
- Migrate to UI-based configuration
- Add to Integrations Manager
- ServiceNow:
- Migrate to UI-based configuration
- Add to Integrations Manager
- Reporting enhancements:
- Word
- Add support for filtering nodes by properties
- Add support for the notextile tag
- Allow multi-word fields/values in the content control filters with double quotes
- Extend support for liquid dynamic content in Word reports
- Warn of missing blank lines around a screenshot only when it’s not the first or last item in a field
- Word
Not using Dradis Pro?
- Automated reports, generate the same reports your clients know and love in a fraction of the time.
- Combine the output from 19+ different tools (including Qualys, Metasploit, Burp…) into a single report.
- Deliver consistent results. Never forget any steps, always know what has been covered and what is still ahead.
- Everyone on the same page: all information available across the team.
- Dradis Pro is reliable, with over 10 years of history, and has a top-notch dedicated support team.